Here You Will Find Some easy steps on How to hack WPA2 wifi password.
Here we will be using kali Linux for this task.You will need a wireless card for this purpose and it should be configured before it can be used.For this purpose, i am going to use Alfa AWUS051NH wireless adapter.You can use any wireless card for this purpose.
First of all, open your kali Linux terminal and type in the iwconfig command.
It will Show you all the wireless cards connected to your system.
The Operating system recognizes a wireless interface named as wlan0
The Next Step Is to enable the wireless interface by using the ifconfig wlan0 up command.
Now I have to see that what wireless networks my wireless card sees.For this purpose issue the iwlist wlan0 scanning command.
The command is used to scan and report all wireless networks in the vicinity.
As You can see that it found a target network: asloWireless Lab also found the MAC address of my access point: 0E:18:1A:36:D6:22 .This is very important to note as I want to limit my attack to a specific target.
Now we can see that the access point is transmitting on the channel 36.This is needy because it allows us to be on a specific wireless channel that our card want to monitor and capture traffic from.
Now we have to change the wireless card mode from managed to monitor.This will allow the wireless card to exmine all the packets in the air.
For this purpose You have to type the airmon-ng start wlan0 command.
now type ifconfig command to verify that the monitor interface is created or not.Now we can see that mon0 is created.
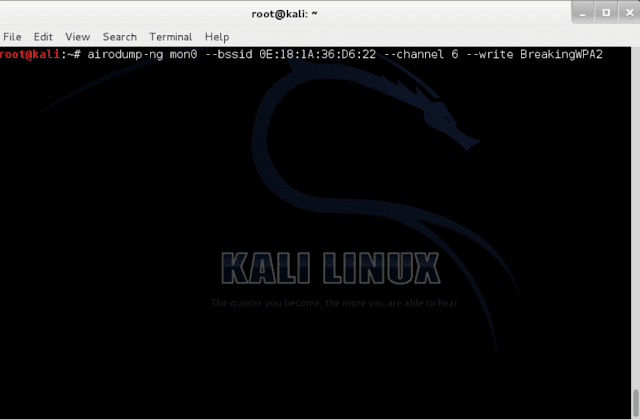
Now next step is to use the airodump-ng cammand to capture the WPA2 handshake.The attacker will have to catch somebody in the act of authenticating to get a valid capture.Airodump-ng will Show a valid handshake when iit captures it.
It will display the handshake confirmation in the upper right hand corner of the screen.
Note: I am going to manually connect to the wireless network to force a handshake.Soon I will Share on how to force a reauthorization to make a device automatically disconnect and reconnect without any manual intervention.
Now We are going to use the following cammand:
airodump-ng mon0 – -bssid 20:aa:4b:1f:b0:10 (to capture packets from our AP) – –channel 6 (to limit channel hopping) – –write BreakingWPA2 (the name of the file we will save to)
airodump-ng mon0 – -bssid 0E:18:1A:36:D6:22 – –channel 36 – –write BreakingWPA2
When you get a handshake:
Example:
Now we will use aircrack-ng with the dictionary file to crack the wifi password.
Use This Command: aircrack-ng “name of cap file you created” -w “name of your dictionary file”
The BreakingWPA2-01.cap is the handshake file.The valid WPA2 handshake airodump captured is stored in the BreakingWPA2-01.cap.
Backtrack 5 came witha basic dictionary. The File darkc0de.Ist is a popular wordlist that came with backtrack 5.We added our password Cisco123 in this file to make the test run a little smoother.
Many Attackers Use large dictionaries that increases the chances of cracking a password.
In this blog we have created a file sample.ISt and added the word Cisco123 in it
Congrats.
If passowrd is found in dictionary by then Aircrack-ng will crack it.